Design secure cloud architecture
Design secure cloud architecture¶
You can secure your cloud environment by introducing specific security zones and domains where you can aggregate such tools as intrusion detection and prevention system, firewall, antivirus, and sandbox for deep data analysis and incident response.
However, it should be noted, that security services nees extra computational resources for which a cloud owner has to pay.
When you consider a deployment of a new security solution or creation of security domain or zone, follow the rule:
Do not invest more resources than the cost of your information assets you
want to protect.
Consider a Security-as-a-Service model to reduce operational costs. According to that model tenants can buy extra security services for some of their projects, if necessary.
Most security threats for cloud users come mostly from guest VMs and external/public networks used to transfer the North-South Internet traffic. However, monitor the East-West traffic as well to detect proliferation and presence of APTs. Attackers can perform internal reconnaissance using Advanced Persistent Threat (APT). For example, scan a tenant network for vulnerable systems and propagate further to take over tenant and provider resources to complete the mission.
To design secure cloud architecture:
Provide users with guidance on securing their workloads up to installing malware defense software in guest OS to mitigate EoP.
Create demilitarized zone (DMZ) when deploying your environment to mitigate EoP.
Note
NIST 800-44 recommends establishing DMZ.
Deploy a Dashboard service on a separate node behind DMZ to mitigate DoS and EoP.
Create a Security Domain for deep traffic inspection and incident investigation to mitigate EoP.
Use network IDPS for both N-S and E-W traffic inspection to reveal network indicators of compromise.
Example of the service leg DMZ architecture with Security Domain
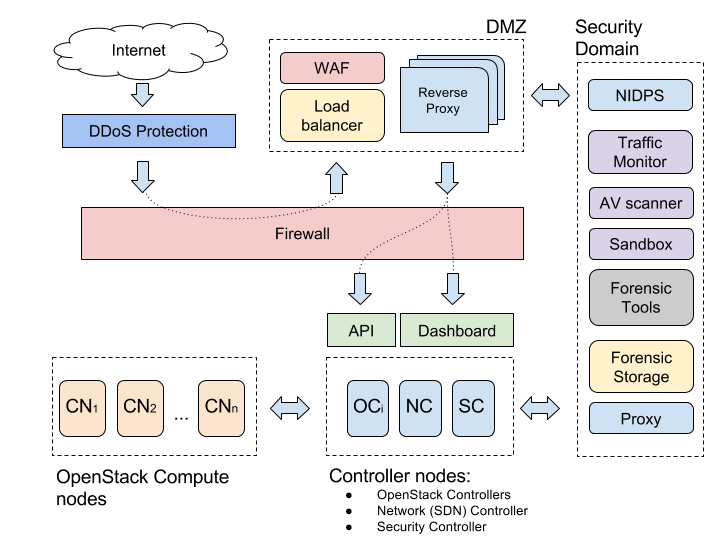
The sections below describe the concepts of the Demilitarized Zone (DMZ) and Security Domain.