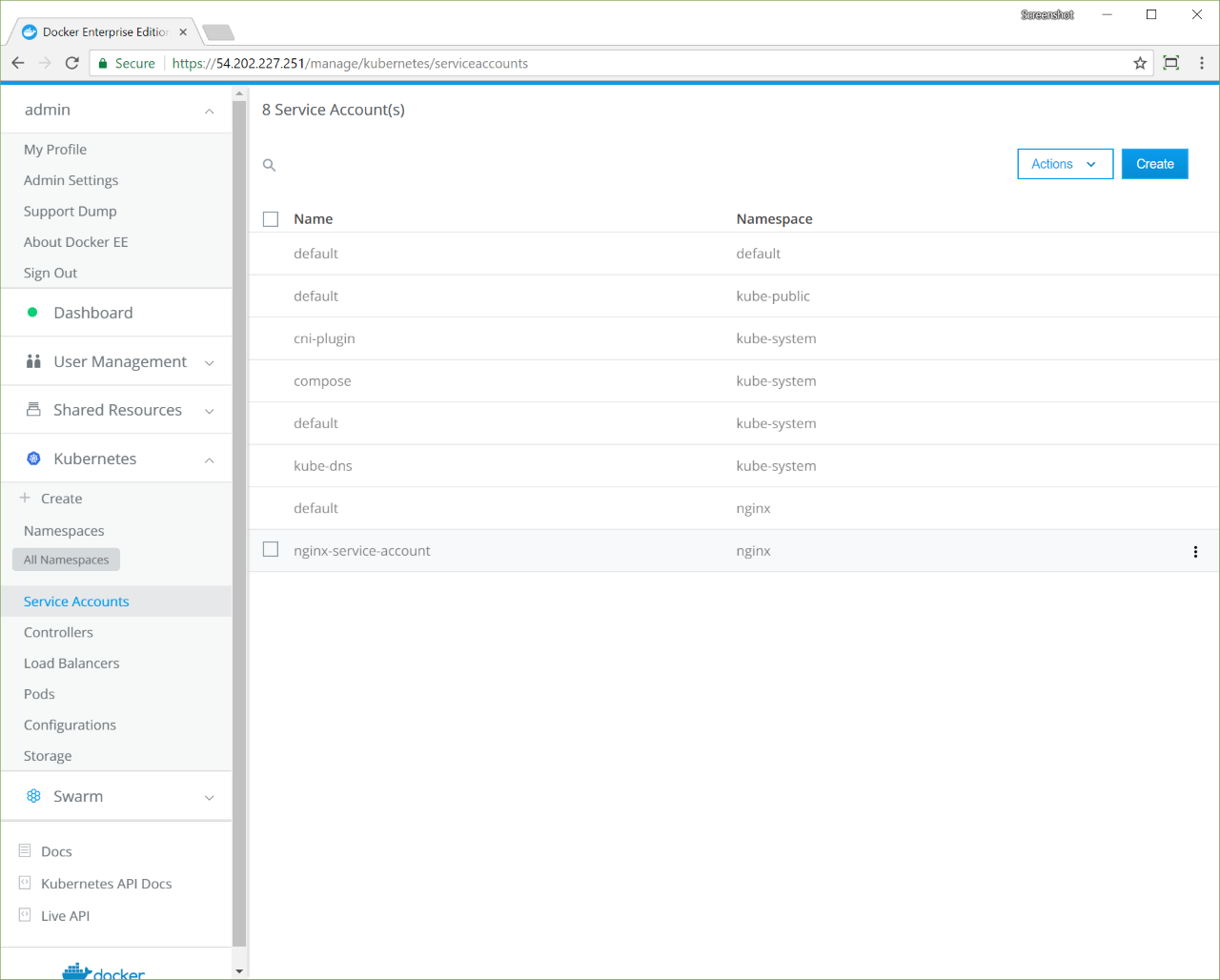
Creating a service account for a Kubernetes app
Creating a service account for a Kubernetes app¶
Kubernetes enables access control for workloads by providing service
accounts. A service account represents an identity for processes that
run in a pod. When a process is authenticated through a service account,
it can contact the API server and access cluster resources. If a pod
doesn’t have an assigned service account, it gets the default
service account.
In Docker Enterprise, you give a service account access to cluster resources by creating a grant, the same way that you would give access to a user or a team.
In this example, you will create a service account and a grant that could be used for an NGINX server.
Create the Kubernetes namespace¶
A Kubernetes user account is global, but a service account is scoped to a namespace, so you need to create a namespace before you create a service account.
Navigate to the Namespaces page and click Create.
In the Object YAML editor, append the following text.
metadata: name: nginx
Click Create.
In the nginx namespace, click the More options icon, and in the context menu, select Set Context, and click Confirm.
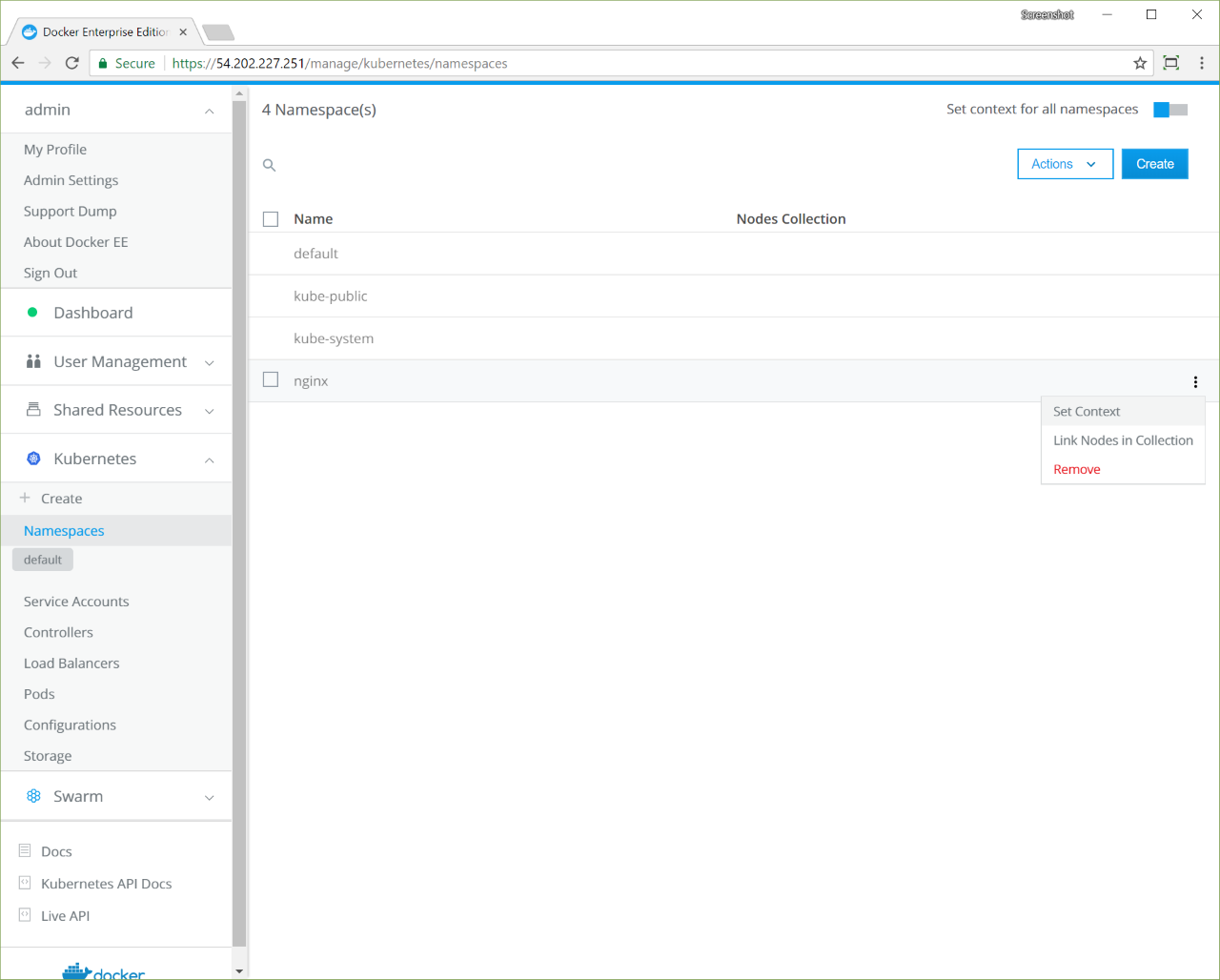
Click the Set context for all namespaces toggle and click Confirm.
Create a service account¶
Create a service account named nginx-service-account in the
nginx namespace.
Create a grant¶
To give the service account access to cluster resources, create a grant
with Restricted Control permissions.
Navigate to the Grants page and click Create Grant.
In the left pane, click Resource Sets, and in the Type section, click Namespaces.
Select the nginx namespace.
In the left pane, click Roles. In the Role dropdown, select Restricted Control.
In the left pane, click Subjects, and select Service Account.
Important
The Service Account option in the Subject Type section appears only when a Kubernetes namespace is present.
In the Namespace dropdown, select nginx, and in the Service Account dropdown, select nginx-service-account.
Click Create.
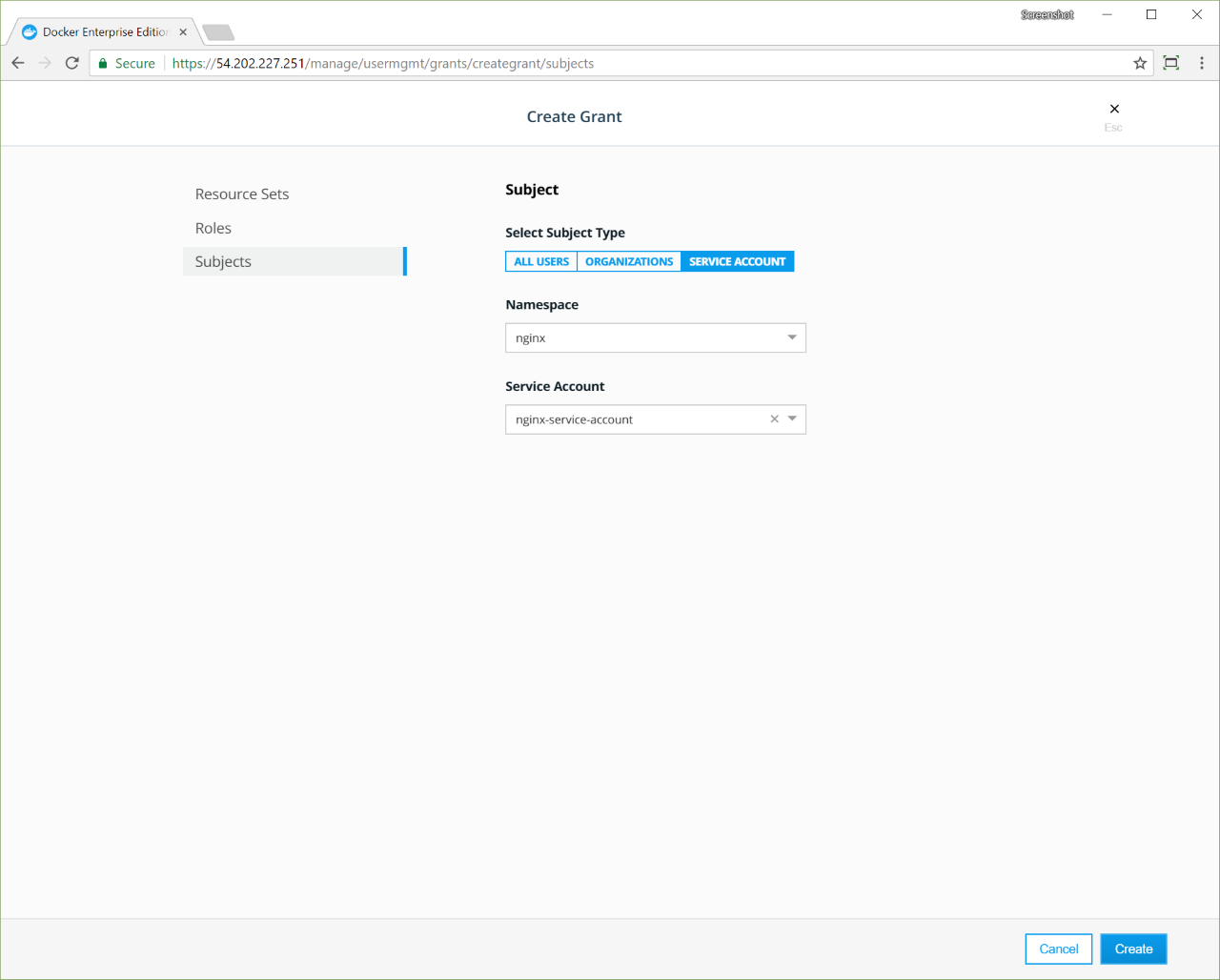
Now nginx-service-account has access to all cluster resources that
are assigned to the nginx namespace.