Investigate and prevent targeted attack (APT)
Investigate and prevent targeted attack (APT)¶
Typically, Advanced Persistent Threats (APTs), as well as backdoors, communicate with C&C servers to get commands from attackers and send back collected information. The network traffic is usually encrypted and sent via a usual http port. This prevents it from being detected by Network Data Leakage Prevention (DLP) or antivirus systems. However, every APT generates a specific traffic that contains unique network IoCs. Based on the analysis of network behavior of recent APTs, it is possible to reveal patterns of targeted attacks to detect still unknown cyber espionage campaign.
For example, the CozyDuke (Office Monkeys) APT
sends http requests to the hacked website acting as a proxy C&C server,
which replies with the specific for the victim set of payload
modules. The transmitted data is Base64 encoded. After taking
Base64 off, the HTTP stream contains a binary content that seems to be
an encrypted executable.
To analyse further, disassemble the backdoor to find out the algorithm (RC4) used for traffic encryption.
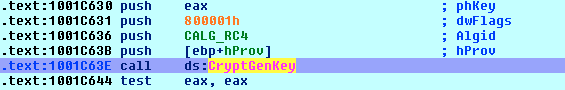
Analysing the code, it is possible to find the RC4 key in the memory when the backdoor exports it in a BLOB format to be stored as a header before the encrypted data. The key is 16 bytes and generated every time a new session is created:
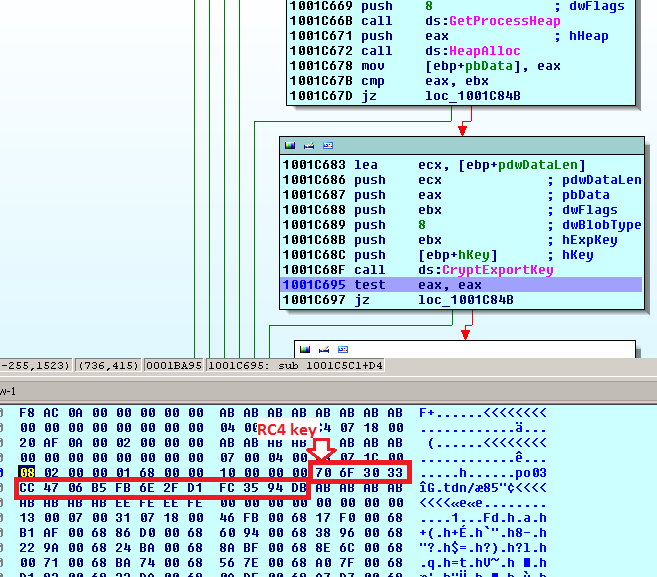
The network packet before being encoded with Base64 contains the key at the beginning, so the server can use it to decrypt the message:
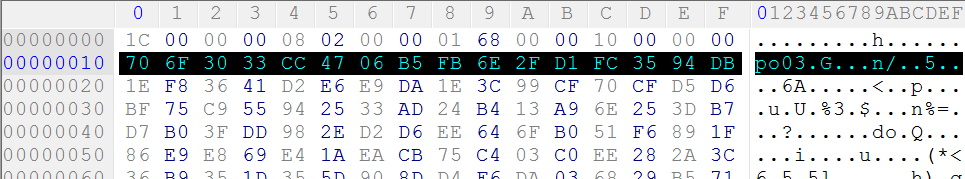
The same key is used to encrypt local configuration file of the backdoor
called racss.dat.
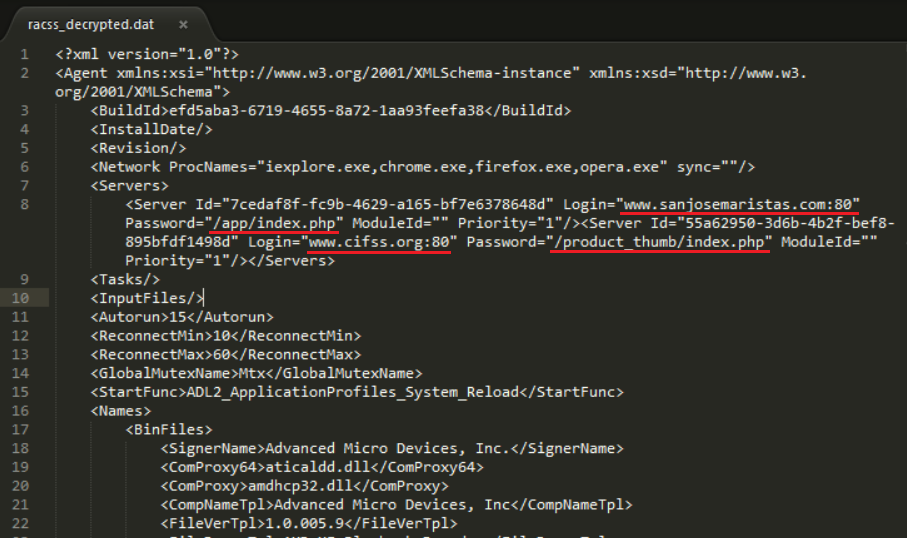
The XML config file shows the C&C proxy server addresses. According to the
information in <Servers> section, two URLs are used to establish
the connection with the C&C proxy, which is merely a someone’s hacked website.
After the short analysis of the threat, network IoCs were found. You can add these network IoCs to the rules of NGFW/IDPS solutions deployed in your cloud. Once blacklists are updated you can monitor if there are more infected machines in a subnet or within a whole cluster.
For incident response, it is important to reveal a security breach and fix it to prevent the penetration in future. In case of the analyzed attack, no exploits were used, but spear-phishing and social engineering methods. In this case, you need to scan SMTP traffic and create rules to block suspicious attached files according to the corporate security policy.
To prevent targeted attacks (APTs):
Terminate TLS on (reverse-)proxy servers for both incomig and outgoing traffic.
Filter out executable and documents from incoming traffic.
Scan the extracted from traffic incoming files with an antivirus solution.
Open the extracted executable and documents from incoming traffic in a sandbox to verify their behaviour for being malicious.
Mirror documents excluding active content such as embedded scripts.
Enable TOR blocking rules on network IDPS.
Note
APTs can communicate with a C&C server in the TOR network. The outgoing TOR traffic can be encapsulted into HTTP and encrypted with TLS to be delivered through a public CDN network to TOR using the domain fronting technique.