Example of threat modeling for Ceph RBD
Example of threat modeling for Ceph RBD¶
The example presents a threat modeling process for Ceph RBD. You can use the Microsoft Threat Modeling Tool to draw a data flow diagram (DFD) and run threat modeling using the STRIDE threat model described in this document.
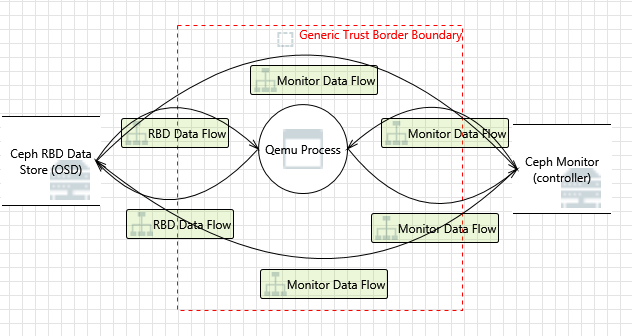
After modeling is completed, the tool suggests a list of potential threats to be mitigated. The tool distributes the discovered threats between interactions. Therefore, the report suggests the list of threats by categories connected to a particular interaction (data flow) on the diagram. Below you can find modeling information by the Microsoft Threat Modeling Tool for each interaction.
An example of threat modeling for the Monitor Data Flow interaction:
Spoofing of Destination Data Store Generic Data Store [State: Not Started] [Priority: High]
Category: Spoofing Description: Ceph Monitor (controller) may be spoofed by an attacker and this may lead to data being written to the attacker’s target instead of Ceph Monitor (controller). Consider using a standard authentication mechanism to identify the destination data store. Justification: <no mitigation provided> Data Store Inaccessible [State: Not Started] [Priority: High]
Category: Denial Of Service Description: An external agent prevents access to a data store on the other side of the trust boundary. Justification: <no mitigation provided> Data Flow Generic Data Flow Is Potentially Interrupted [State: Not Started] [Priority: High]
Category: Denial Of Service Description: An external agent interrupts data flowing across a trust boundary in either direction. Justification: <no mitigation provided> Potential Excessive Resource Consumption for OS Process or Generic Data Store [State: Not Started] [Priority: High]
Category: Denial Of Service Description: Does Qemu Process or Ceph Monitor (controller) take explicit steps to control resource consumption? Resource consumption attacks can be hard to deal with, and there are times that it makes sense to let the OS do the job. Be careful that your resource requests don’t deadlock, and that they do timeout. Justification: <no mitigation provided> Data Flow Sniffing [State: Not Started] [Priority: High]
Category: Information Disclosure Description: Data flowing across Monitor Data Flow may be sniffed by an attacker. Depending on what type of data an attacker can read, it may be used to attack other parts of the system or simply be a disclosure of information leading to compliance violations. Consider encrypting the data flow. Justification: <no mitigation provided> Data Store Denies Generic Data Store Potentially Writing Data [State: Not Started] [Priority: High]
Category: Repudiation Description:https://www.microsoft.com/en-us/sdl/adopt/threatmodeling.aspx Ceph Monitor (controller) claims that it did not write data received from an entity on the other side of the trust boundary. Consider using logging or auditing to record the source, time, and summary of the received data. Justification: <no mitigation provided> The Generic Data Store Data Store Could Be Corrupted [State: Not Started] [Priority: High]
Category: Tampering Description: Data flowing across Monitor Data Flow may be tampered with by an attacker. This may lead to corruption of Ceph Monitor (controller). Ensure the integrity of the data flow to the data store. Justification: <no mitigation provided> Authenticated Data Flow Compromised [State: Not Started] [Priority: High]
Category: Tampering Description: An attacker can read or modify data transmitted over an authenticated dataflow. Justification: <no mitigation provided>
See also